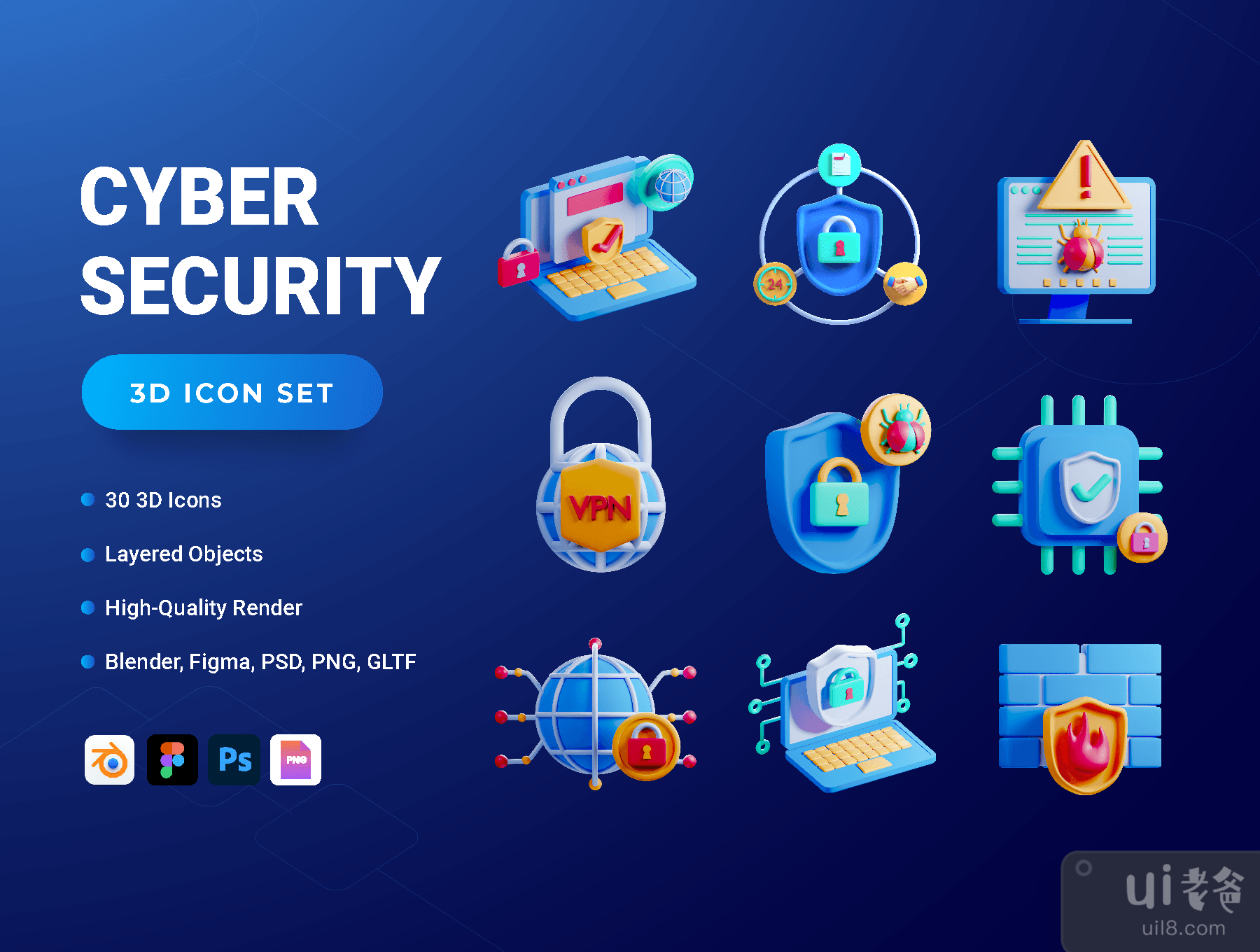
30个3D网络安全图标集 (30 3D Cyber Security Icon Set)



-中文-
概述想要推广您的网络安全服务?希望提高对在线安全的认识?出色的视觉效果更容易吸引人们。介绍 30 3D 网络安全图标集。
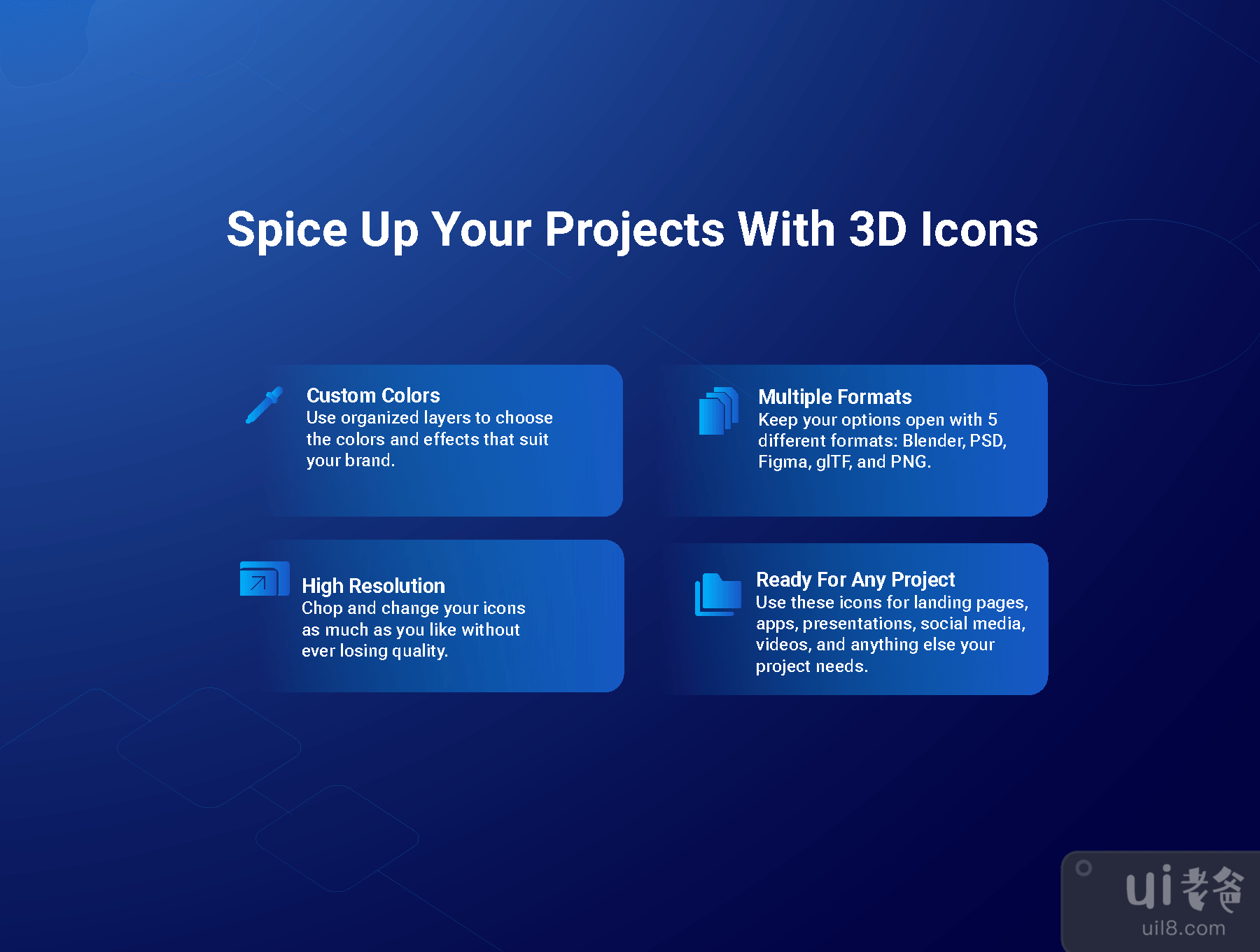
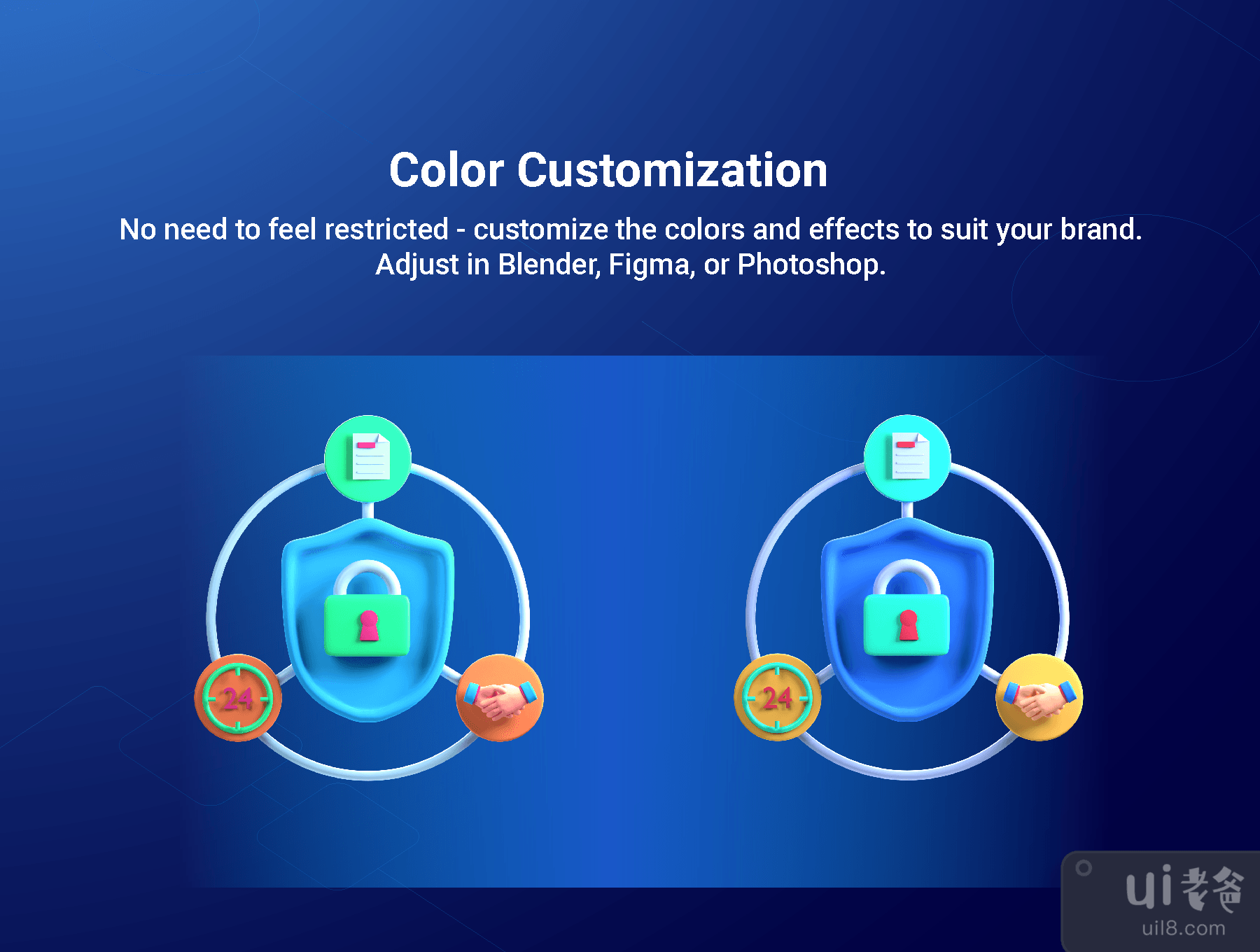
除了出色的 3D 设计外,这些图标还可以自定义!更改它们的形状、大小和颜色,使它们完美适合您的项目。享受!
TL;DR:30 个 3D 网络安全图标。利基特定,完全可定制。 5种格式。
包含的格式:Blender、Figma、GLTF、PNG、PSD
你得到的图标:
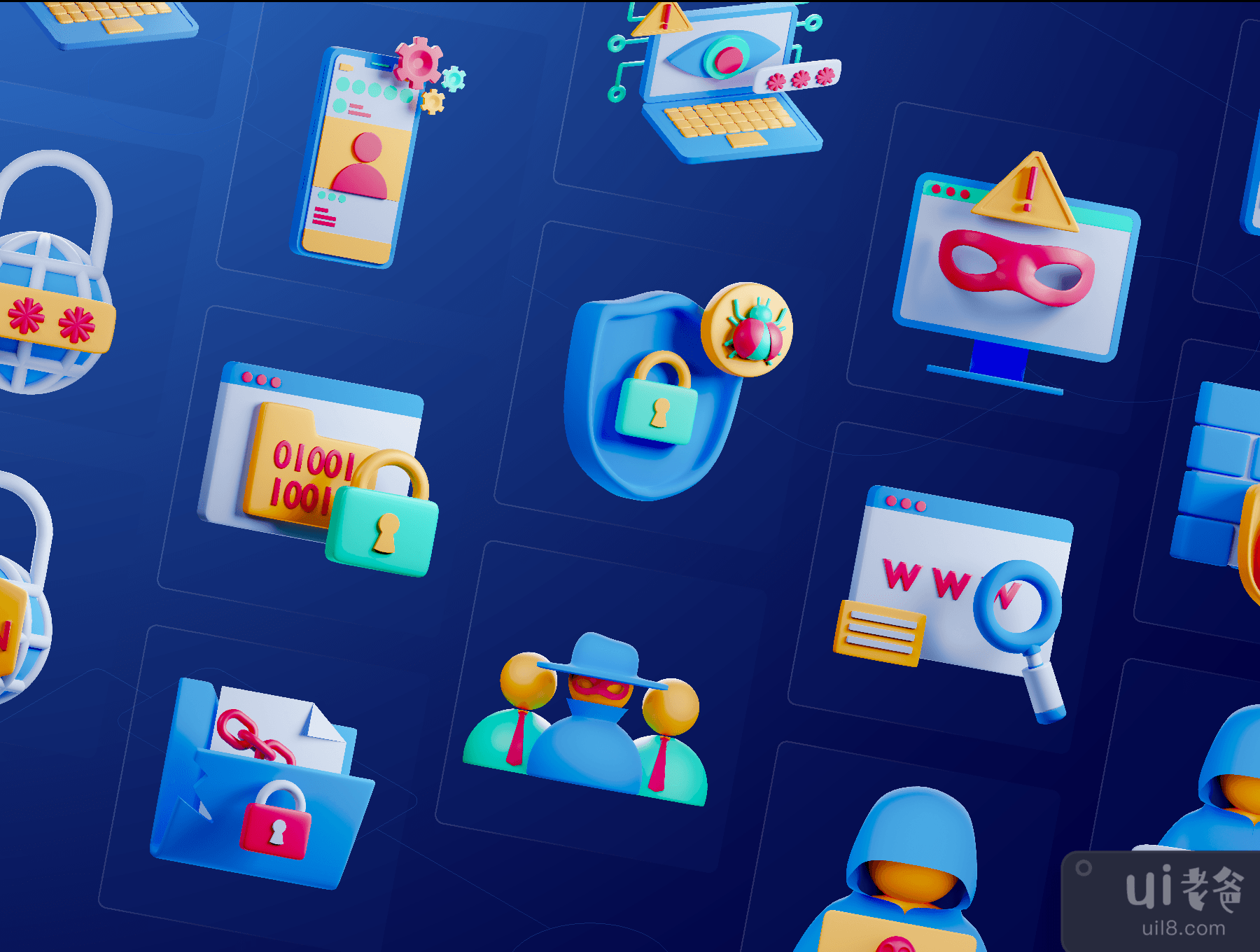
网络安全、CIA 三合会、网络威胁、硬件安全、软件安全、云安全、网络安全、移动安全、端点安全、零信任、病毒、恶意软件、勒索软件、网络钓鱼、中间人 (MITM) 攻击、分布式拒绝服务 (DDoS) 攻击、帐户接管 (ATO)、黑客攻击、内部威胁、数据泄露、虚拟专用网络 (VPN)、防火墙、域、防病毒、加密、密码、IP 地址、Rootkit、间谍软件、社会工程学
为什么选择我们的图标?
图标结构:每种文件格式都在其自己的文件夹中,以方便您使用。
注重细节:每个图标都完美到单个像素。我们仔细检查。
客户支持:如果您遇到任何类型的问题,我们会尽快提供帮助。
我们的客户说:
“我喜欢这些图标,尤其是因为它们的组织和命名让你不必四处寻找你想要使用的图标。” - 米歇尔
“这些太棒了!种类繁多,组织得很好。” - ktaylor310
“非常棒的图像 - 超级甜美和吸引人,非常适合我想要的。我喜欢它们有多种图像类型,而且非常易于使用。” - thefulljennyHighlights30 个 .BLEND 格式的网络安全图标1 .Fig 格式的 30 个网络安全图标 .PNG 格式的 30 个网络安全图标 .Psd 格式的 30 个网络安全图标 .GLTF 格式的 30 个网络安全图标100% 可定制且易于使用的格式 1.4 GB in1 文件
-英文-
OverviewWish to promote your cyber security services? Looking to raise awareness about online safety? Reaching people is easier with great visuals. Introducing the 30 3D Cyber Security Icon Set.
In addition to their awesome 3D design, these icons can be customized as well! Change their shape, size, and color, and make them perfect for your project. Enjoy!
TL;DR: 30 3D cyber security icons. Niche-specific, fully customizable. 5 formats.
Formats included: Blender, Figma, GLTF, PNG, PSD
Icons you’re getting:
Cyber Security, CIA Triad, Cyberthreat, Hardware Security, Software Security, Cloud Security, Network Security, Mobile Security, Endpoint Security, Zero Trust, Virus, Malware, Ransomware, Phishing, Man-in-the-middle (MITM) Attack, Distributed Denial-of-Service (DDoS) Attack, Account Takeover (ATO), Hacking, Insider Threat, Data Breach, Virtual Private Network (VPN), Firewall, Domain, Antivirus, Encryption, Password, IP Address, Rootkit, Spyware, Social Engineering
Why choose our icons?
Icon structure: Each file format in its own folder for your ease of use.
Attention to detail: Every icon is perfect down to a single pixel. We double-check that.
Customer Support: If you face any type of problem, we’ll help fast.
Our customers say:
“I love these icons, especially because they are organized and named so that you don't have to dig around to find the one you want to use.” - michellellc
“These are great! Wide variety and very well organized.” - ktaylor310
“Really great images - super sweet and appealing and perfect for what I wanted. I love that they come in multiple image types and are so easy to use.” - thefulljennyHighlights30 Cyber Security Icons in .BLEND Format1 Cyber Security Icons in .Fig Format30 Cyber Security Icons in .PNG Format30 Cyber Security Icons in .Psd Format30 Cyber Security Icons in .GLTF Format100% Customizable and easy to useFormat1.4 GB in1 File




